Safeguarding water distribution systems against terrorist threats
A new on-line monitoring system, developed by Hach Homeland Security Technologies to detect and mitigate an attack on water distribution systems, is undergoing advanced testing by the US Army.
The vulnerability of drinking water supplies to assault by terrorists gained widespread attention since the 11 September 2001 World Trade Center attack in the USA. Distribution systems remain an accessible and tempting target even though most supply sources have limited vulnerability due to the massive volumes of water involved. Terrorists could compromise a system through an assault anywhere in the distribution network through a backflow event. This vulnerability cannot be addressed by improving physical security given the size and scope of most distribution systems. Distributed monitoring is the only way to detect and mitigate the effects of such an attack.
The ability to detect an event in the distribution system and then identify it would be of incomparable value in responding to an incident in a timely and proper manner. The general scientific consensus is that no practical, available, or cost-effective real-time technology exists to detect and mitigate intentional attacks or accidental incursions in drinking water distribution systems.
Over the past several years a new approach has been developed to address the problems of distribution system monitoring. The developed system employs an array of common analytical instrumentation, such as pH and chlorine monitors, coupled with advanced interpretive algorithms to provide detection/classification-response networks that are capable of enhancing distribution system security and operations. The instrumentation has been found effective against a variety of agents including TICs (toxic industrial chemicals), TIMs (toxic industrial materials), and chemical and biological warfare agents.
The response of these various agents is not only adequate to detect the presence of a contaminant, but the responses elicited from the sensor array allows for the possibility of classification. Through the use of a searchable library of agent profiles, the system provides not only an alarm, but also a classification of the likely cause. The profiles of more than 80 of the most likely threat agents and common contaminants have been compiled. In addition, a proprietary baseline estimator immediately reduces unknown warnings due to regular fluctuations in operational parameters upon start-up. As time since deployment increases, the number of unknown deviations from baseline rapidly reduces to near zero by the system’s programmed ability to learn what is normal for a given operation.
Selecting parameters to be measured
A variety of instrumentation technologies could be used in the system, such as MEMs technology, lab on a chip, GC-MS, and Raman Spectroscopy. Hach wanted to create a cost-effective system that could be rapidly deployed and was robust in operation and diverse in its ability to detect contaminants, so the developers decided to investigate the possibility of using a variety of well characterised, off-the-shelf sensors proven to be robust for field deployment in a multi-parameter array. The sensors chosen for investigation were pH, conductivity, chlorine residual, turbidity, and total organic carbon (TOC). Data was collected for oxidation-reduction potential (ORP), but it was not used in the final system because the probes are unstable and prone to fouling in long-term installations.
Problem with real world date
Real world baseline data is not always as neat and tidy as a laboratory system. Significant fluctuations can occur on a regular basis in real world systems. The problem then becomes, can we differentiate between the changes that are seen as a result of the introduction of a contaminant and those changes that are a result of everyday system perturbation?
The secret to success in this situation is to have a robust and workable baseline estimator. Extracting the deviation signals in the presence of noise is absolutely necessary for good sensitivity. Several traditional methods of baseline estimation were investigated and found to either degrade sensitivity or result in unacceptable numbers of false positives. Finally, a proprietary method was derived and found to be effective.
How the trigger system works
In the system, signals from all instruments are processed from a five-space vector to a scalar trigger signal. The signal then goes through the proprietary baseline estimator. A deviation of the signal from the estimated baseline is then derived; a gain matrix is applied, and then compared to a threshold level
Real world data was obtained from several sites and the most noisy data stream for each parameter was selected and used to test the system. Even with extremely noisy data the trigger signal typically remains below a threshold level set at 1. Therefore; during normal operation, with no agent present, the typical process deviation should not be large enough to produce a Trigger Signal > 1. However, the trigger level of 1 is easily exceeded when the data for a cyanide incursion at 1% of the LD-50 or approximately 2.8 mg/L is superimposed on the system. Other contaminants exhibit similar results. The results are even more dramatic when the amount of cyanide in the system is increased to 10% of the LD-50 (Graph 1).
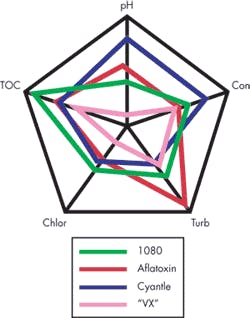
The deviation vector that is derived from the trigger algorithm contains significantly more data than what is needed to simply trigger the system. The Deviation Vector’s magnitude relates to concentration and Trigger Signal, while the Deviation Vector direction relates to the agent characteristics. Seeing that this is the case, laboratory agent data can be used to build a Threat Agent Library of Deviation Vectors. A Deviation Vector from the water monitor can be compared to Agent Vectors in the Threat Agent Library to see if there is a match within a tolerance. This system can be used to classify the agent when present. Each vector results in a vector angle in n-space that is representative of the class of chemical present. Graph 2 is a radar plot of some agent data that visually illustrates this point. The direction of the vector is unique for a given class of agent, allowing the algorithm to classify the cause of a trigger.
Conclusion
The system uses robust, off-the-shelf sensor technologies by placing them together in an array and using intelligent algorithms in a new and powerful manner to extract data that is used in devising an early warning system for water security. The system is an invaluable security tool for recognising system incursions, but it has the ability to become much more. To date, most of the library work has been done on threat agents, but the libraries will be eventually expanded to incorporate common distribution system problems that may arise. Hach expects the system to become a useful tool in evaluating day-to-day system health and operational parameters.
The system is currently undergoing advanced testing using threat agents at the US Army’s Proving Grounds in Aberdeen, Maryland, and has recently undergone Environmental Technology Verification testing by Battelle at the US Environmental Protection Agency’s Test and Evaluation Facility in Cincinnati, Ohio.
Author’s Note
Dan Kroll is the chief scientist for Hach Homeland Security Technologies, located in Loveland, Colorado, USA.
Threats to water supply systems
• May 1983: Israel uncovers Israeli Arab plot to poison Galilee water with “an unidentified powder”.
• February 2002: Al Qaeda arrested with plans to attack U.S. embassy water in Rome with “cyanide”.
• December 2002: Al Qaeda operatives arrested with plans to attack water networks surrounding Eiffel Tower neighbourhoods in Paris
• April 2003: Jordan foils Iraqi plot to poison drinking water supplies from Zarqa feeding U.S. military bases along the Eastern desert.
• September 2003: FBI bulletin warns of Al Qaeda plans found in Afghanistan to poison US food and water supplies.
Captions to graphs, tables:
1. Graph 1. Trigger Signal 1% LD50 Cyanide
2. Graph 2. Radar Plot of Agent Deviations
3. Table 1. MDLs for Selected Agents as a Percentage of LD-50