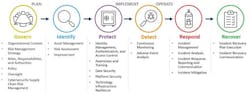
Beyond America's Water Infrastructure Act of 2018 (AWIA): advancing from cybersecurity assessment to managing cybersecurity and resilience
Cybersecurity stakes are high for a water/wastewater utility. They face many challenges such as protecting public and employee welfare, protecting the environment, regulations and asset protection — to name a few. Attacks on critical infrastructure are on the rise from a number of threat actors such as disgruntled former employees, organized crime (ransomware), foreign hacking groups, and even nation states. The recently released joint cybersecurity advisory co-authored by CISA, NSA, FBI, EPA, DOE, TSA, and more regarding Volt Typhoon is yet another wake up call.
Fortunately, there are multiple ways to evaluate supervisory control and data acquisition (SCADA) system cybersecurity. Each yields good value, but when used alone, might miss important vulnerabilities. This article describes a multi-layered strategy to reduce cybersecurity risk and improve resilience using several common practices. A relevant healthcare analogy would be the use of more than one test (e.g., screening, X-ray, blood work) to assess overall health.
Cyber axiom #1: diagnose before you prescribe
The cybersecurity assessment is an essential starting point. It is typically interview-based and comprised of questions that assess the status of recommended cybersecurity controls and countermeasures. There are plenty of free-to-use assessment tools and frameworks available depending upon the utility’s desired level of cyber scrutiny.
EPA has its Water Cybersecurity Assessment Tool (WCAT) with 33 controls. AWWA has its Water Sector Cybersecurity Risk Management Tool with 100 controls. Both of those tools were written for the water sector which includes wastewater. There are also sector-agnostic standards (e.g. NIST SP800-53, NIST SP800-82, ISA/IEC 62443) that can be customized to a utility’s unique needs and offer many additional controls.
The cybersecurity assessment helps a utility understand its degree of compliance to a standard. It is a significant step in the direction toward an overall cybersecurity strategy, but it is just the beginning. What utilities need most is an assessment that is broad enough in scope to create the vision, establish the gap and prioritize remediation tasks into a clear roadmap — a “Cybersecurity Master Plan.”
Cyber axiom #2: pick a standard and clearly define what “done” looks like
A good strategy establishes a common vision. A good start is the creation of a “SCADA Cybersecurity Governance Committee” that develops and maintains SCADA cybersecurity policies. Those policies should align with applicable federal and state regulations, the utility’s desired level of cyber-risk reduction, industry best practices and consider constraints the utility faces such as budget, resources and expertise. The goal is a right-sized policy that adequately manages risk and is achievable and sustainable.
Cyber axiom #3: If you can’t draw it, you don’t understand it ... and if you don’t understand it, you can’t protect it
A significant part of cybersecurity is managing connectivity. So, the second part of establishing the vision involves creating an asset inventory of hardware and software along with a matching current-state network architecture drawing.
This drawing must illustrate SCADA-to-SCADA and SCADA-to-External network connectivity, the routers/firewalls that connect those networks and the application data flow crossing those network boundaries. Your main objective is to understand, approve of, tightly control and protect that data flow. At this point you can have some productive discussions on how to mitigate (reduce) cybersecurity risk; often the simple addition of a well-placed firewall or demilitarized zone (DMZ) can significantly reduce cybersecurity risk.
The last step in establishing the vision is to create a future-state network architecture drawing. As a side note, the asset inventory usually includes patching levels and forms the foundation of a vulnerability management strategy — an entire article unto itself.
Cyber axiom #4: ”You can’t manage what you don’t measure.” – Peter Drucker
Once the vision is established, an audit (similar to the assessment previously described) will help to establish the “gap” between a utility’s paper policy/future-state networking drawings and “SCADA system reality.” That gap is then analyzed, prioritized and organized into a remediation plan that aims to reduce risk as much as possible, as soon as possible.
Cyber axiom #5: How do you know? You start by testing
A penetration test can help reveal vulnerabilities that are otherwise difficult to identify. The objective is to understand if a cyber adversary could gain unauthorized access to critical networks and systems using common tactics. Whereas the other methods in this article are non-intrusive, one should assume this method is intrusive and exercise great caution.
It is very important to note that a lot of products, particularly older industrial automation products, can be negatively affected by the use of even the simplest of available software tools. This is why it is so important to contract with an experienced SCADA penetration testing firm, establish a clear scope, have spare products on hand, and backups ready that you know will work.
Cyber axiom #6: IT Risk does not equal OT Risk. So, they must be treated differently and appropriately
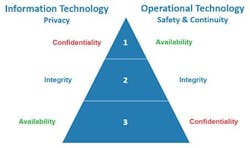
There are three cybersecurity objectives – confidentiality (C), integrity (I) and availability (A). Whereas information technology (IT) cybersecurity priorities are C-I-A, operational technology (OT) cybersecurity priorities are A-I-C. This is because OT cybersecurity solutions seek to ensure life/safety and operational continuity of critical infrastructure.
The Cyber-Informed Engineering (CIE) and Consequence-driven Cyber-informed Engineering (CCE) methodologies developed by Idaho National Labs offer yet another option and help address cyber-safety. CIE is the proactive approach applied during engineering design projects for new systems (i.e. greenfield) and includes traditional cybersecurity controls. CCE is the reactive approach used with existing systems (i.e. brownfield) and focuses less on traditional cybersecurity solutions because it begins with the assumption that the adversary has already penetrated your SCADA network.
Both methodologies have the distinction of using an analysis of physical plant processes and the application of engineering principles to “engineer out” or “reduce the effects of” undesirable scenarios that could result from a cyberattack. The “non-digital” mitigations may include pressure relief valves, check valves, minimally-sized chemical feed pumps, hardwired variable frequency drive controls, etc. Both methodologies help support the duty we all have to protect public and employee welfare — the biggest difference between IT and OT cybersecurity.
SCADA cybersecurity is not an easy problem to solve. It is not five things you do; it is more like 500 micro steps. Utilities must explore the many options for assessing SCADA cybersecurity to find the right solution for their unique environment. These approaches can also be combined to discover new remediation opportunities to achieve a higher level of cybersecurity risk reduction. By implementing a multi-layered strategy to reduce cybersecurity risk, utilities are not only helping to protect their business operations, but they are helping to safeguard the communities that rely on their services.
About the Author

Jim Schultz
Jim Schultz, PE, CISSP, CCNA, GICSP, CISA, C|EH is a Senior Operational Technology Cybersecurity Consultant with Black & Veatch. He has more than 30 years of experience with utility and federal projects aimed at improving OT and reducing cybersecurity risk to critical infrastructure. Throughout his career, Jim has been engaged in the planning, design, implementation, and support of OT and IT projects in the water, wastewater, manufacturing, electric utilities and federal sectors, including the U.S. Department of Defense.